A decades-old HTTP authentication technique has been spotted making the rounds in Netflix themed smishing attacks.
Summary
Recently I saw a tweet from SwiftOnSecurity showing a smishing attempt that used an interesting technique leveraging HTTP Basic Authentication to alter the appearance of a link.
Smishing
Smishing is a type of social engineering attack where attackers use SMS (text messaging) to trick victims into giving away sensitive information, downloading malware, or taking other actions that benefit the attackers.
Understanding HTTP Basic Authentication
HTTP Basic Authentication is a widely used method of authentication that is used by web applications and websites to protect resources from unauthorised access. It is considered a simple and straightforward mechanism that is widely supported by web servers and clients.
The way HTTP Basic Authentication works is by requiring users to provide a username and password combination separated by a colon (:).
While HTTP Basic Authentication is a simple and widely supported authentication mechanism, it has some security limitations. For example, the username and password are transmitted in plaintext, making them vulnerable to interception and eavesdropping.
Abusing HTTP Basic Authentication Syntax
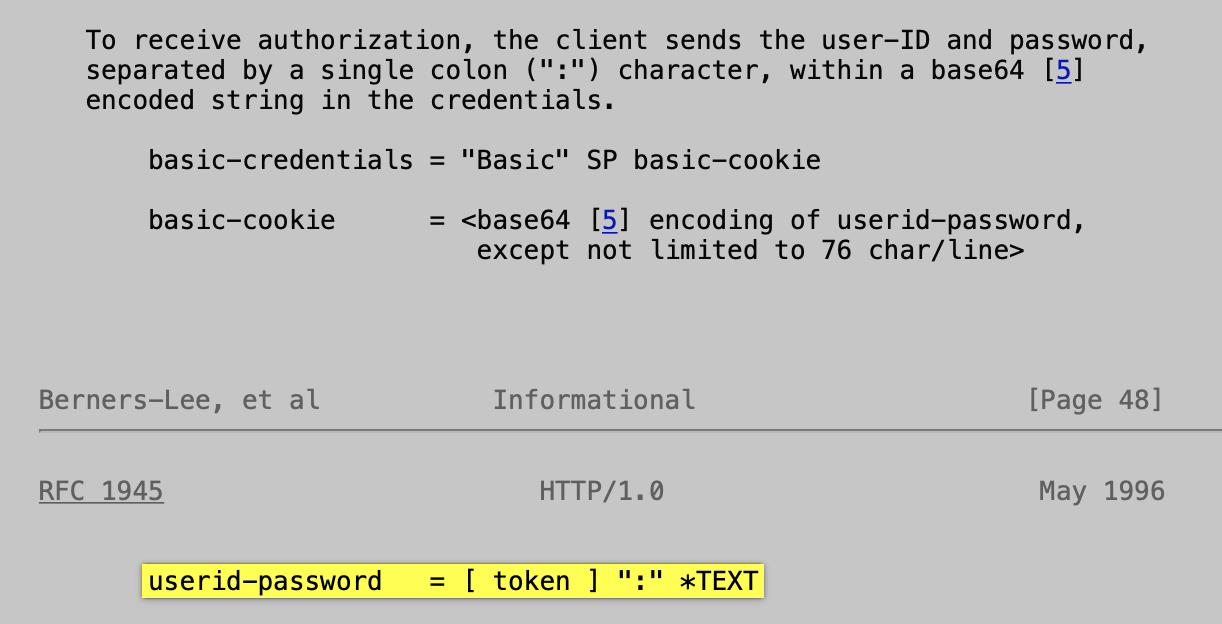
Data Type definition
The Basic Authentication Scheme section of the Request for Comments Memo for Hypertext Transfer Protocol defines the datatype for the userid-password parameter as *TEXT.
Meaning that the HTTP Basic Authentication username and password inputs can include all characters except for the colon (:) character used to separate the two fields.
Leveraging this information
With this information, a number of interesting URLs can be crafted.
Without breaking the HTTP Basic Authentication syntax we can generate convincing links that route to our malicious domain.
http://WWW.SAFE_SITE:COM@BAD_SITE.COM/
# Username: WWW.SAFE_SITE
# Password: COM
# Link : BAD_SITE.COM
http://microsoft.com:[email protected]/
# Username: microsoft.com
# Password: 1
# Link : apoc.work
http://www.google.com.account.login:[email protected]/
# Username: www.google.com.account.login
# Password: .
# Link : apoc.work
2001 SANS Paper
Back in 2001 SANS released a Global Information Assurance Certification Paper that made reference to several examples of HTTP basic authentication syntax exploitation.
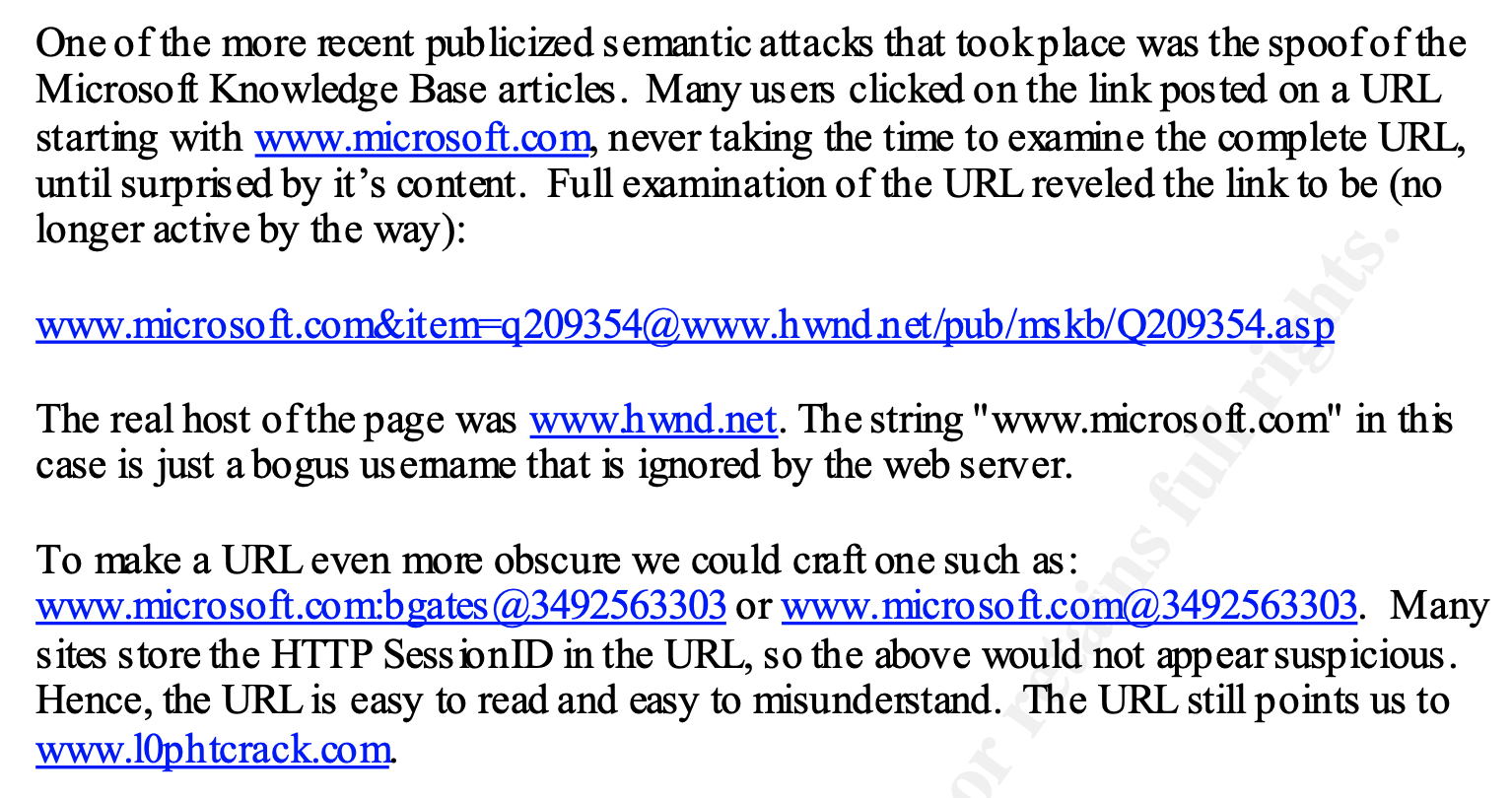
An interesting second layer, seen above, is the usage of IP Address decimal notation to craft the link parameter in the URL.
Suspicious users would still have a hard time identifying an issue with the URL, with this additional technique.
Decimal IP Address Notation
Decimal IP address notation is a way of representing IP addresses in decimal form, without the use of dots to separate the numbers.
In this notation, each byte of the IP address is represented as a decimal number between 0 and 255, and the four bytes are combined to form a single decimal number.
For example, the IP address 192.168.1.1 in decimal notation is represented as the number 3232235777. To convert from decimal notation to dotted-decimal notation, we need to split this number into four bytes and convert each byte to its corresponding decimal number.
Decimal IP address notation is not commonly used in networking, as it is less human-readable than dotted-decimal notation and is not widely supported by networking tools and equipment. However, it can be useful in certain applications, such as when working with databases or other systems that store IP addresses as decimal numbers.
In The Wild
The tweet mentioned earlier included an example of a threat actor using this technique to trick victims into clicking a that looks to route to a Netflix domain.
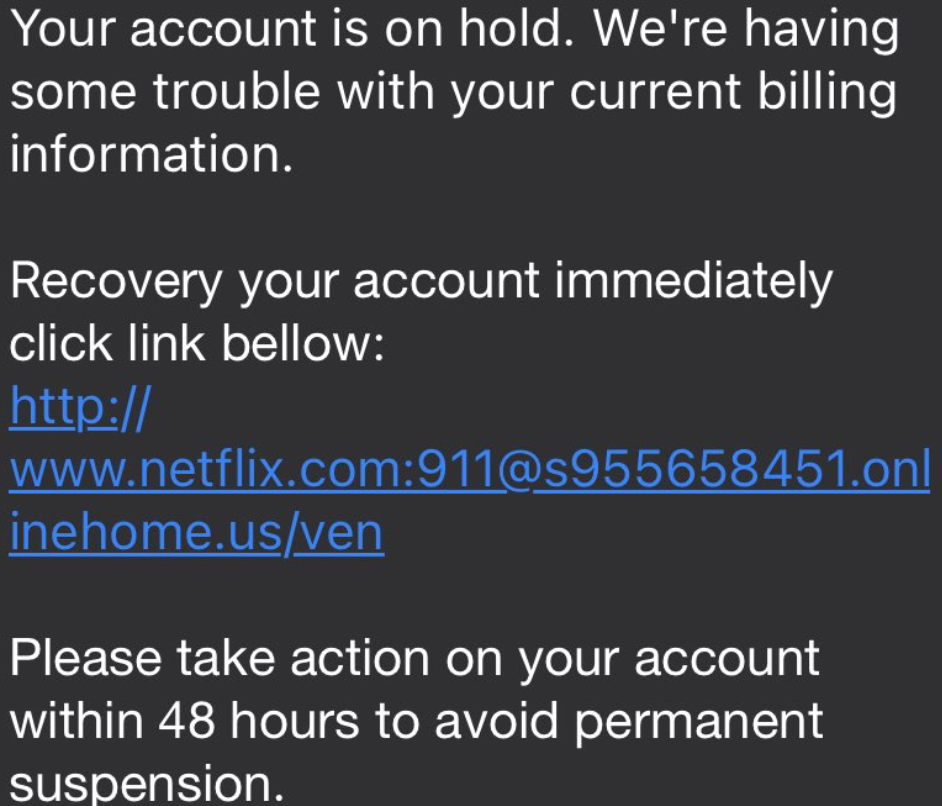
The typical user awareness advice, given to individuals, potentially confuses the identification of phishing/smishing attacks leveraging this technique.
Looking at the domain, it appears that the root domain is www.netflix.com, followed by characters that may be seen, by most users, as the start of the path : OR @.
Potentially resulting in successful user deception.
Conclusions
In conclusion, HTTP Basic Authentication is a decades-old method of authentication that is rarely used by modern web applications and websites. However, precisely because of this disconnect, it could see a resurgence as an effective attack vector against unsuspecting users.
While modern web applications have moved on to more secure and sophisticated authentication mechanisms, HTTP Basic Authentication remains supported by many web servers and clients. This means that attackers can use this technique to craft convincing links that appear to be legitimate, and trick users into clicking on them.
References
2001 SANS Paper - Global Information Assurance Certification Paper