Summary
What is a Subdomain Takeover?
A subdomain takeover occurs when an attacker is able to gain control over a subdomain on a victim’s domain. This is typically caused by a misconfigured canonical name (CNAME) in the Domain Name System (DNS) pointing to a service no longer in use. Taking control of the service will result in control of the subdomain.
In the context of this writeup, the GymShark domain (de-headless.staging.gymshark.com) had a CNAME record pointing to a Shopify domain that was no longer in use. Claiming the Shopify domain resulted in a full subdomain takeover.
The Bug
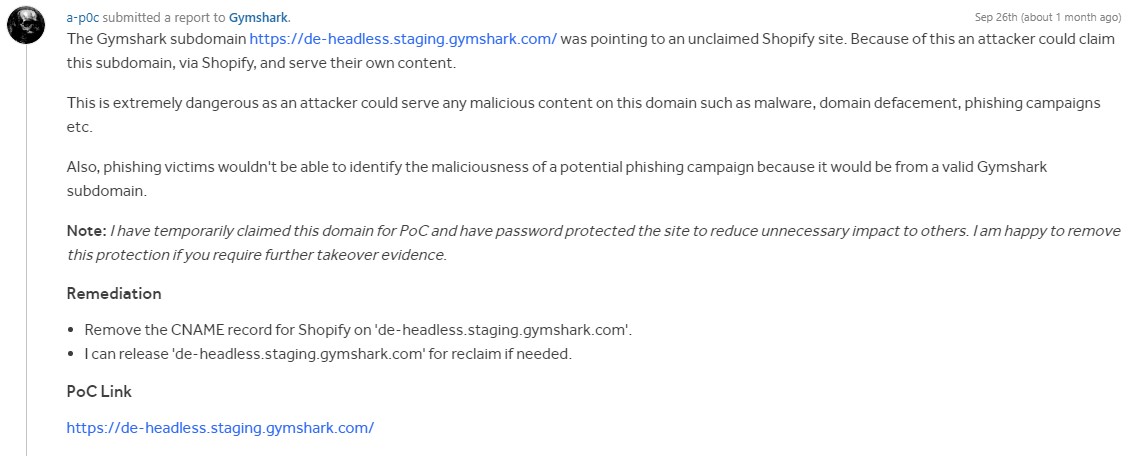
https://hackerone.com/reports/1711890
Scanning in-scope assets led me to the subdomain (de-headless.staging.gymshark.com). The site returned a generic Shopify ‘Only One Step Left’ page and viewing the CNAME records verified that the domain was reflecting the contents of an unclaimed Shopify site.
Claiming the Shopify site allowed me to host content on the GymShark subdomain via the Shopify site. A successful subdomain takeover!
The finding was accepted and remediated by GymShark as a High severity (CVSSv3 7.5) bug.
Finding the bug
Enumeration
Approaching the program, my first step was to enumerate all in-scope assets (including subdomains) to increase my attack surface and give me a better understanding of GymShark’s public facing infrastructure. One way to enumerate subdomains was crt.sh, using it to retrieve all connected subdomain certificates relating to a root domain.
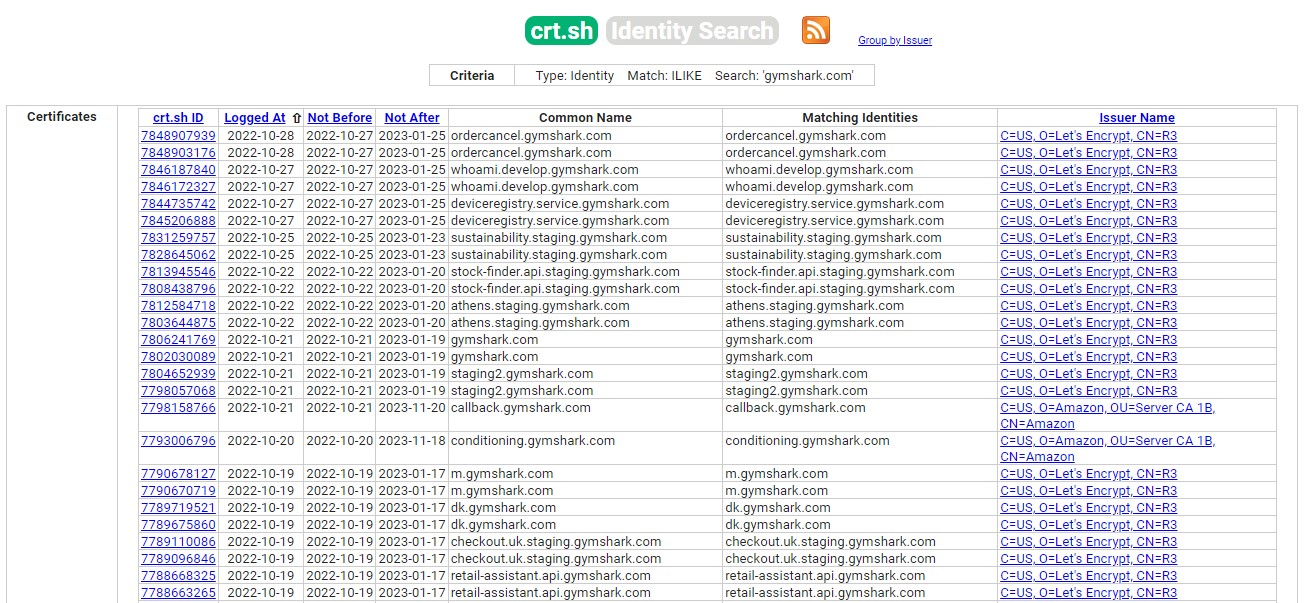
Using a custom bash script (below), I collected a list of subdomains for the root domain (gymshark.com).
domain=gymshark.com;curl -fsSL "https://crt.sh/?q=${domain}" | pup 'td text{}' | grep "${domain}" | sort -n | uniq | httprobe > /tmp/enum_tmp.txt; python3 EyeWitness.py -f /tmp/enum_tmp.txt --web
Note: Custom bash command used to enumerate certificate subdomains via crt.sh. Running the subdomains through EyeWitness (A Python tool for screenshotting domains) I began working my way through the hundreds of images, looking for anything interesting to focus on first.
Shopify ‘Only One Step Left’
One of the screenshots was a Shopify branded ‘Only One Step Left’ page on a staging subdomain (de-headless.staging.gymshark.com).
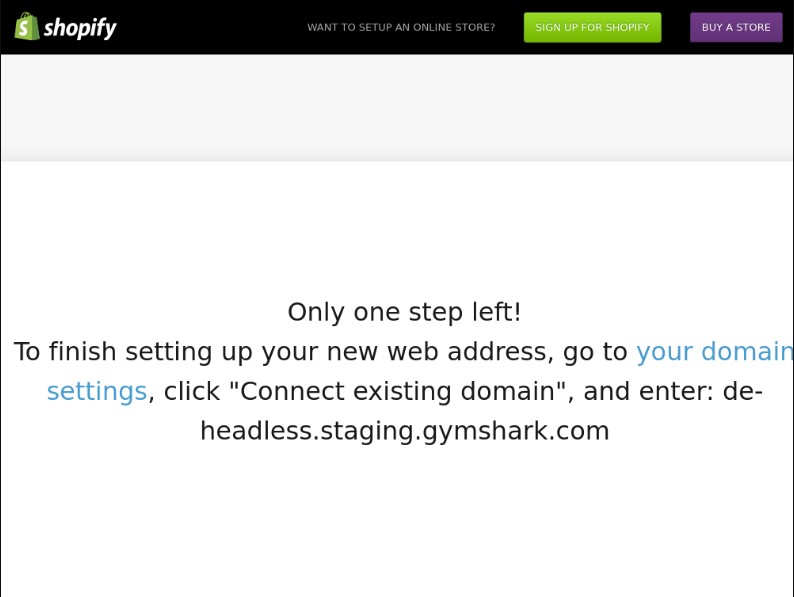
This Shopify message is usually displayed on a shop site just before the user connects it to the serving domain.
The CNAME configuration on the subdomain contained an entry pointing to the unclaimed Shopify site. So, the person in control of the Shopify site content would be in control of the subdomain content too!
PoC
To verify my findings of a subdomain takeover, I needed to take control of the Shopify site referenced in the subdomain CNAME entry.
I signed up to Shopify and created a basic PoC (Proof of Concept) site.

I then added the GymShark subdomain (de-headless.staging.gymshark.com) to my Shopify site configuration.
Refreshing the GymShark subdomain now displayed the contents of my PoC site, the subdomain takeover was successful!
I now had full control over the content hosted on the GymShark subdomain!
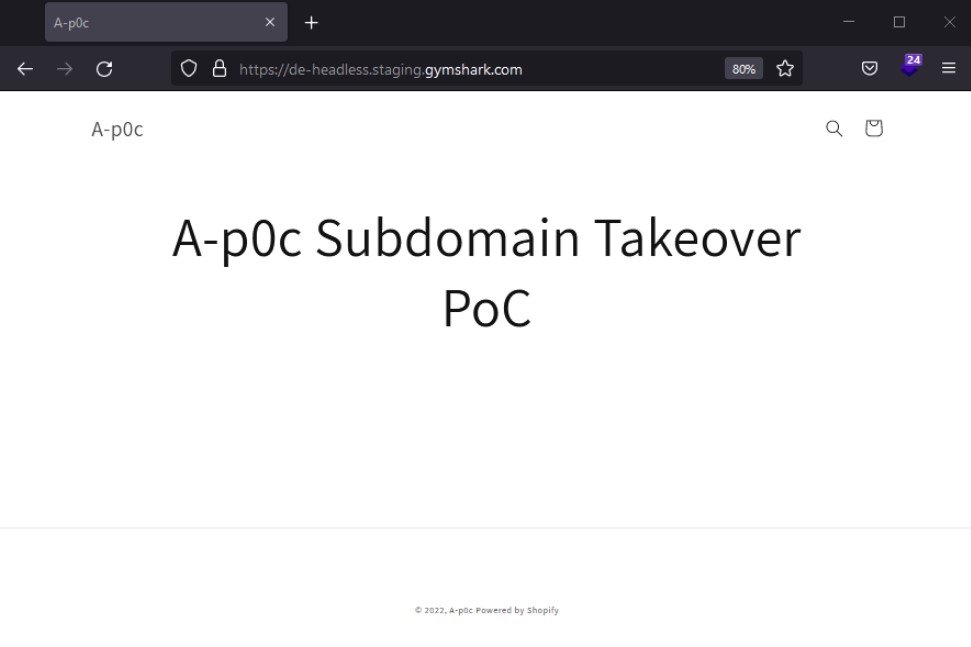
Report
After securing the Shopify page with a temporary password (to reduce any impact to GymShark), I reported the bug.

The next day, the bug had been triaged and remediated by the GymShark security team (Removing the CNAME record from the subdomain).
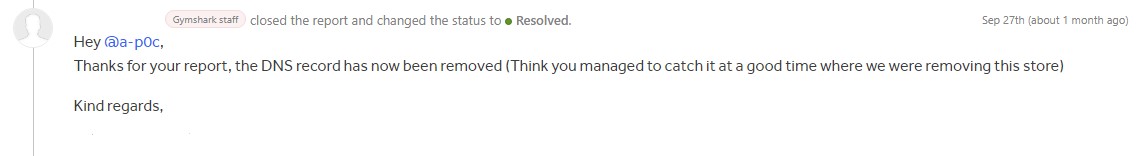
Made the HackerOne hacktivity front page!